I am building a team's configurable tab. As part of the requirement, I need to implement SSO and then call MS Graph API calls to get the list of user in the team.
I am following the below artical that explains the entire flow:
https://www.youtube.com/playlist?list=PLWZJrkeLOrbZ3uG8Xb8yOUeWu7UDu4Q_-
So far, I am succesfully able to perfom the SSO as mentioned in the following 2 videos: https://www.youtube.com/watch?v=J3KCjpZGiEI&list=PLWZJrkeLOrbZ3uG8Xb8yOUeWu7UDu4Q_-&index=2
https://www.youtube.com/watch?v=TRfZDx7N6Fw&list=PLWZJrkeLOrbZ3uG8Xb8yOUeWu7UDu4Q_-&index=4
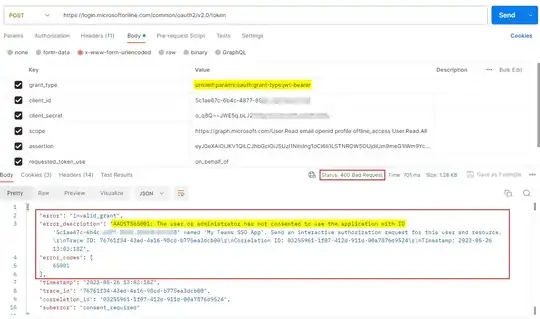
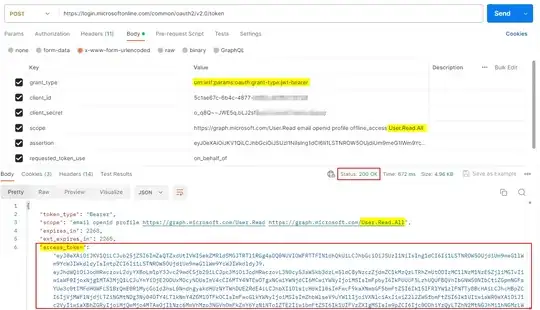
I am able got the ID Token + Access Token from SSO but when I am trying to exchange this token to get the Graph API access token (as mentioned in https://www.youtube.com/watch?v=E6bbyPVK8Q0&list=PLWZJrkeLOrbZ3uG8Xb8yOUeWu7UDu4Q_-&index=5), I am getting the following error:
AADSTS65001: The user or administrator has not consented to use the application with ID <webapi_ app_id>.
I went through the comment mentioned in the following stack overflow post, but it didn't resolve my issues:
AADSTS65001: The user or administrator has not consented to use the application with ID <app-id>
Here is my code to get the Graph API access token:
const clientId = {clientId};
const clientSecret = {clientSecret};
const SSOToken = req.query.ssoToken
const aadTokenEndPoint = `https://login.microsoftonline.com/${
jwtDecode<any>(SSOToken).tid
}/oauth2/v2.0/token`;
const oAuthOBOParams = {
grant_type: "urn:ietf:params:oauth:grant-type:jwt:bearer",
client_Id: clientId,
client_secret: clientSecret,
assertion: SSOToken,
requested_token_use: "on_behalf_of",
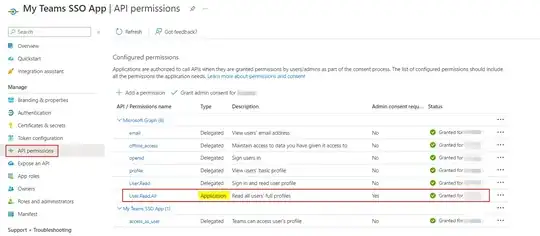
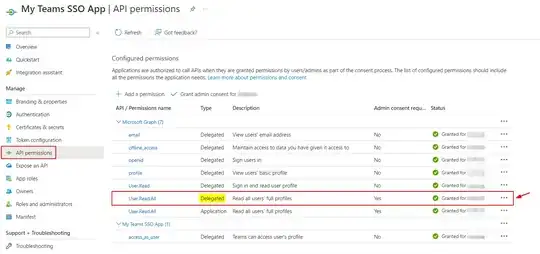
scope: "https://graph.microsoft.com/User.Read email openid profile offline_access User.Read.All",
};
const oAuthOboRequest = Object.keys(oAuthOBOParams)
.map((key, index) => `${key}=${encodeURIComponent(oAuthOBOParams[key])}`)
.join("&");
const HEADERS = {
accept: "application/json",
"content-type": "application/x-www-form-urlencoded",
};
log({ HEADERS, oAuthOboRequest, oAuthOBOParams, aadTokenEndPoint });
try {
const response = await axios.post(aadTokenEndPoint, oAuthOboRequest, {
headers: HEADERS,
});
log(response);
if (response.status === 200) {
res.status(200).send(response.data);
} else {
if (
response.data.error === "invalid_grant" ||
response.data.error === "interaction_required"
) {
res.status(403).json({ error: "consent_required" });
} else {
res.status(500).json({ error: "Could not exchange access token" });
}
}
} catch (error) {
res.status(400).json({ error: `unknown error ${error}` });
}
**Authentication - I just added the URL but I does not have the auth-end receiving point in server **
Accepting the Pop-up permission
Postman