I am building a MS Teams tab application that utilizes the SSO and Graph API. It will be published in App Store for commercial use. I had trouble implementing that and ask question here and it got resolved. Here is the question link: (MS Graph API AADSTS65001: The user or administrator has not consented to use the application with ID <app-id>)
I am successfully able to test it within my organization and i can retrieve the user list using Graph API.
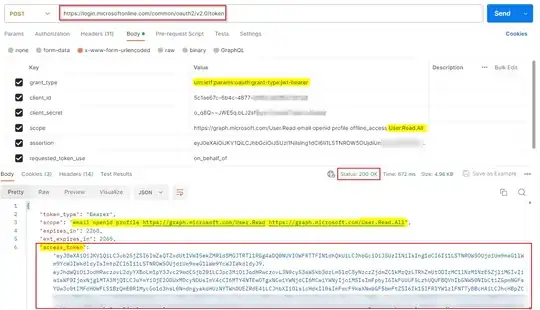
Before starting the publishing process, I was trying to test it with another organization and it did not work. I am able got the ID Token + Access Token from SSO for other organization but when I am trying to exchange this token to get the Graph API access token It gave me the same error i.e.
MS Graph API AADSTS65001: The user or administrator has not consented to use the application with ID <app-id>
Since this not working for that other organization, I am fearing that it won't work if I publish it and will give the same error message.
Since it's working correctly with my organization, I am not sure what I am missing here and why it does not work with the other organization.
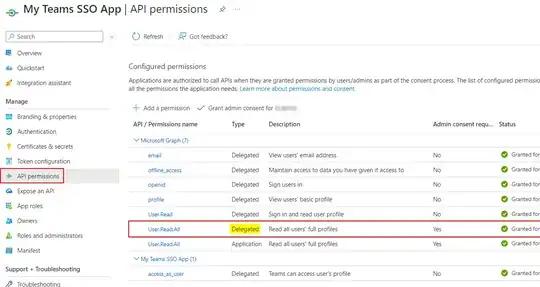
Here is API permission: I removed all the permission that requires admin consent just to check if that works.
 Any help would be appreciated. Thanks!
Any help would be appreciated. Thanks!